Configure an Impersonation Account to User Mailboxes
Create a user account to use specifically for the purpose of using for the Email Tracking service. This account will need to be given Application Impersonation permission on all OnePlaceMail user mailboxes. Either make this account with a password that doesn’t expire, or ensure you have procedures in place to ensure passwords are updated so that an expired password scenario is not encountered.
Option 1: Grant access to Impersonate All Users
Use the following procedure to give the service account permission to impersonate any user. The same procedure applies to Exchange on-premises and Exchange Online (Office 365)
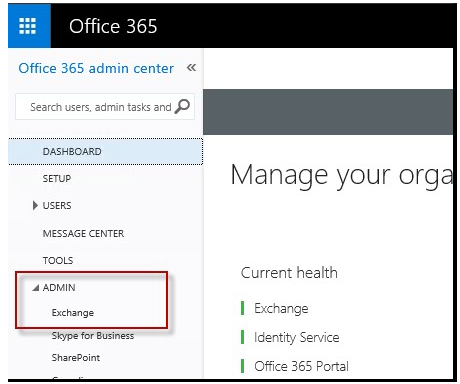
- Open the Exchange Admin Center (this is available from the Admin application in Office 365 as shown below)
- Select Permissions | Add
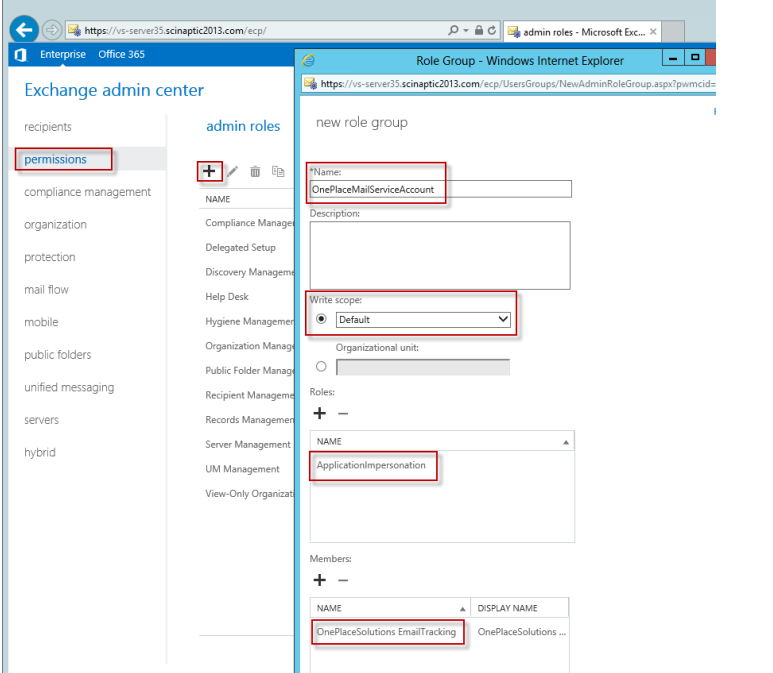
Please take note of these considerations
- Write Scope: Select Default. This determines which mailboxes the permission applies to, Default includes all mailboxes within the scope.
- Roles: Select ApplicationImpersonation. This is the type of permission to grant to mailboxes within the write scope
- Members : Specify the name of your service account (OnePlaceSolutions EmailTracking) that is going to be connecting to all the mailboxes and performing the updates. Effectively we are granting this user the ability to impersonate within mailboxes within the write scope.
Option 2: Grant Access to Impersonate Limited Users
Granting impersonation access to a limited set of Exchange users is more complex than granting access to all users. In Exchange this requires the creation of a Management Scope which identifies the users that the impersonation will apply to.
The remainder of this section details how to create a Management Scope that is bound to a Group. While this is conceptually an easier example to understand, it may not be suitable for your environment due to the following reasons:
-
Management scopes bound to a group does not support nested groups
-
Management scopes bound to a group use the full distinguished name of the group, in Office 365 Microsoft reserve the right to change the distinguished name of a group to support restructuring and you may have no control or warning over this.
-
A full explanation of Exchange Management Scopes is beyond the scope of this document and it is recommended that you familiarize yourself with the options available. The following MSDN article is a good starting point.
-
Understanding management role scope filters: https://technet.microsoft.com/en-us/library/dd298043(v=exchg.150).aspx
Create the Management Scope -
Launch the Exchange Management Shell.
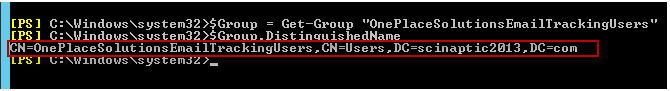
First we need to get the distinguished name of the group we are going to use (this is the distribution group we just created). The easiest way to do this is to get a handle on the group object and then read out the distinguished name.
$Group = Get-Group "OnePlaceSolutionsEmailTrackingUsers"
$Group.DistinguishedName
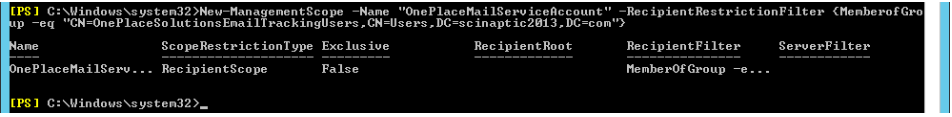
Use the following command to create the new management scope now that you have the distinguished name of the group.
New-ManagementScope –Name "OnePlaceMailServiceAccount" –RecipientRestrictionFilter {MemberofGroup -eq "your-distinguished-group-value-here"}
Now that we have the new Management Scope defined I like to test it by running the following command which will list out all the users that are included in this Management Scope. This should be the users that you have added to the distribution group.
$myMS = (Get-ManagementScope | Where-Object Name -eq "OnePlaceMailServiceAccount")
Get-Recipient -RecipientPreviewFilter $myMS.RecipientFilterReturn to the Exchange Admin Center
Select Permissions | Admin Roles | Add New Role Group
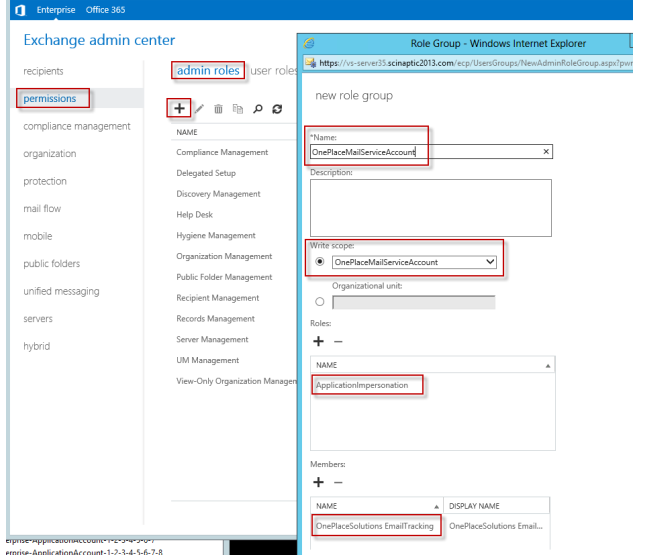
The important information on the New Role Group dialog are:
- Write Scope – Select the new Management Scope (OnePlaceMailServiceAccount) we created. This determines which mailboxes the permission applies to.
- Roles – Select ApplicationImpersonation. This is the type of permission to grant to mailboxes within the write scope.
- Members – Specify the name of your service account (OnePlaceSolutions EmailTracking) that is going to be connecting to all the mailboxes and performing the updates. Effectively we are granting this user the ability to impersonate within mailboxes within the write scope.
| Next Step: Configure Email tracking software |
